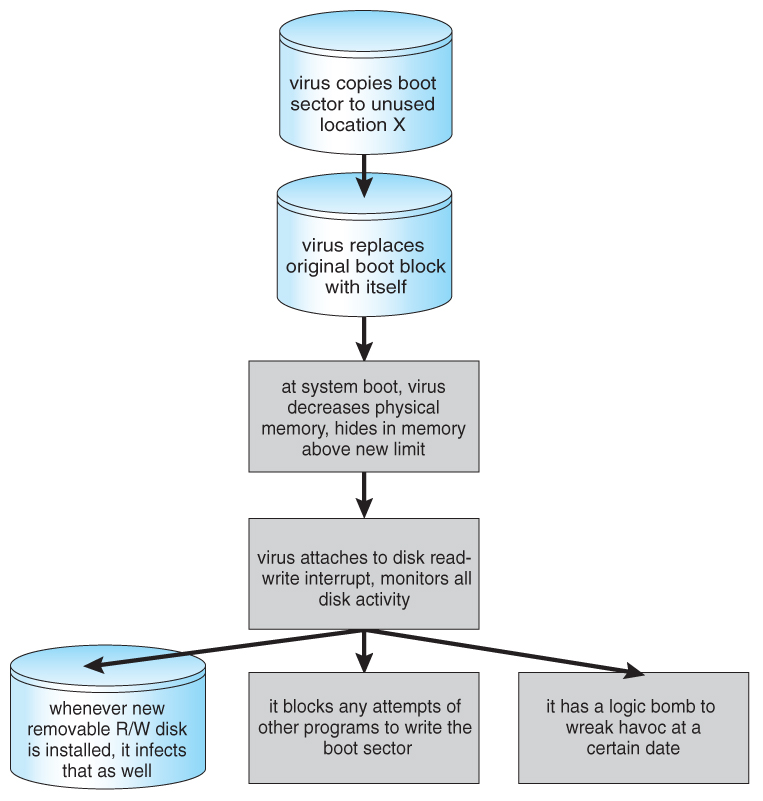
Diagram Of Virus In Computer
Functional Diagram Of A Computer Virus Which Has Search Copy And

 Example Of The Attack Tree For Computer Viruses Download
Example Of The Attack Tree For Computer Viruses Download
 State Machine For Computer Virus Spreading Download Scientific
State Machine For Computer Virus Spreading Download Scientific
 Pseudo Code Of A Computer Virus 1 Download Scientific Diagram
Pseudo Code Of A Computer Virus 1 Download Scientific Diagram
 An Attack Tree For A Computer Virus Download Scientific Diagram
An Attack Tree For A Computer Virus Download Scientific Diagram
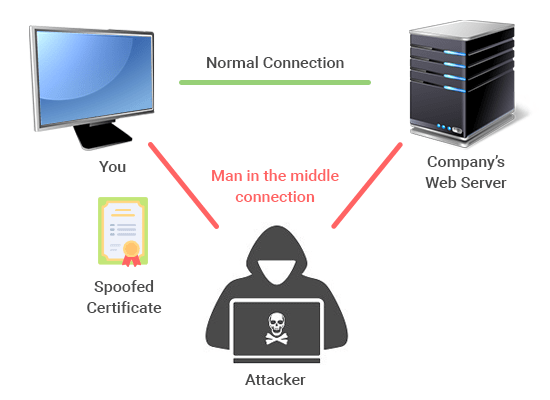 What Does A Malware Virus Do Different Types Of Malware
What Does A Malware Virus Do Different Types Of Malware
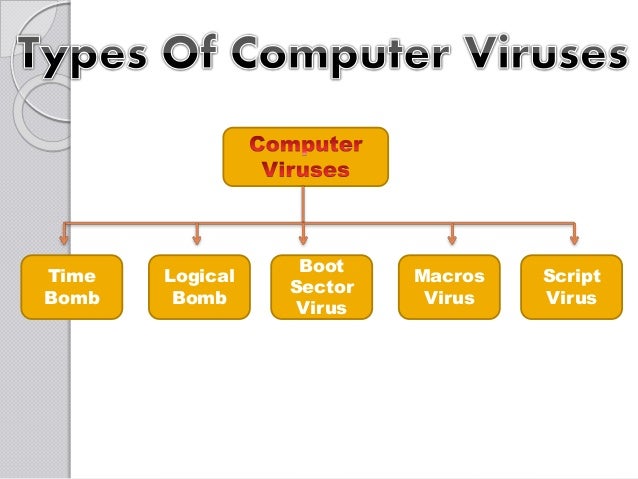
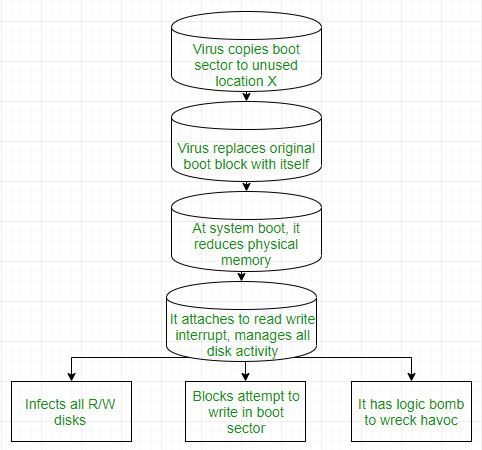 Types Of Viruses Geeksforgeeks
Types Of Viruses Geeksforgeeks
 State Machine For Computer Virus Spreading Download Scientific
State Machine For Computer Virus Spreading Download Scientific
 What Is A Computer Virus Definition Types Protection
What Is A Computer Virus Definition Types Protection
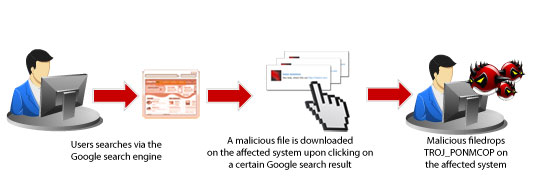 Understanding The Printer Virus Threat Encyclopedia Trend
Understanding The Printer Virus Threat Encyclopedia Trend
 Computer Virus Images Stock Photos Vectors Shutterstock
Computer Virus Images Stock Photos Vectors Shutterstock
What You Need To Know About Computer Viruses Ack Security
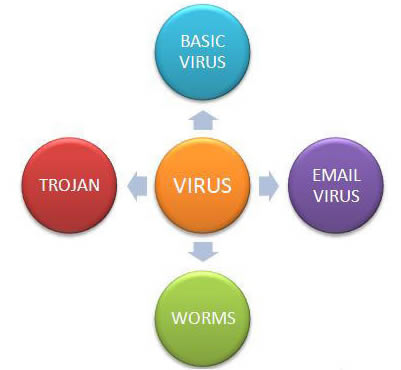 Types Of Computer Viruses And Other Online Threats Pc Pros 2 Go
Types Of Computer Viruses And Other Online Threats Pc Pros 2 Go

 Uml Diagram Of Embedded Target Profile And Annaakournikova
Uml Diagram Of Embedded Target Profile And Annaakournikova
 Computer Virus Images Stock Photos Vectors Shutterstock
Computer Virus Images Stock Photos Vectors Shutterstock
![]() Alert Antivirus Attack Computer Virus Business Flow Chart
Alert Antivirus Attack Computer Virus Business Flow Chart
 Patent Report Us9906550 Computer Virus Protection
Patent Report Us9906550 Computer Virus Protection
Computer Virus Computer Virus Diagram
 Computer Virus Attack Royalty Free Vector Image
Computer Virus Attack Royalty Free Vector Image
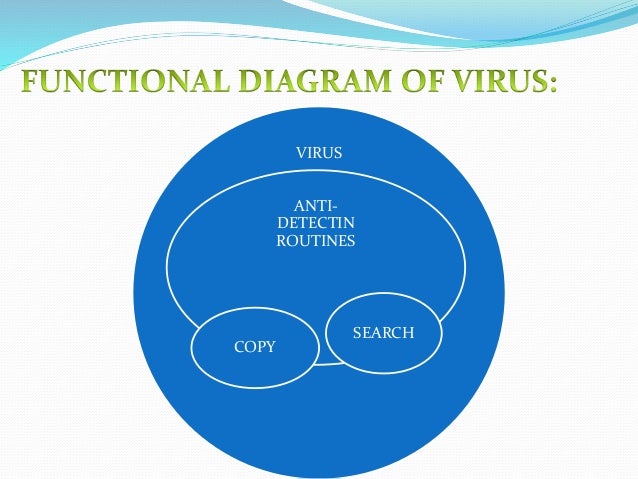 Presentation On Computer Virus
Presentation On Computer Virus
 Example Of The Attack Tree For Computer Viruses Download
Example Of The Attack Tree For Computer Viruses Download
 Ipa Information Technology Promotion Agency Japan Ipa Isec In
Ipa Information Technology Promotion Agency Japan Ipa Isec In
 Cybercrime Banking Virus Zeus Strikes Back Comsec Global
Cybercrime Banking Virus Zeus Strikes Back Comsec Global
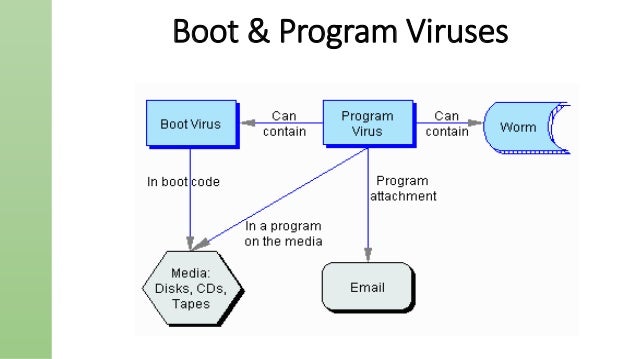 Computer Viruses And Protections
Computer Viruses And Protections
 Computer Virus Removal Pctechbytes
Computer Virus Removal Pctechbytes
Computer Trojan Horse Virus Information
 Old Habits Die Hard Detecting And Removing Computer Virus With Ocaml
Old Habits Die Hard Detecting And Removing Computer Virus With Ocaml
 Virus A Retrospective Social Impact
Virus A Retrospective Social Impact
 Computer Virus Images Stock Photos Vectors Shutterstock
Computer Virus Images Stock Photos Vectors Shutterstock
 Ipa Information Technology Promotion Agency Japan Ipa Isec In
Ipa Information Technology Promotion Agency Japan Ipa Isec In
![]() Alert Antivirus Attack Computer Virus Business Flow Chart
Alert Antivirus Attack Computer Virus Business Flow Chart
Computer Virus Protection Diagram Schematic And Image 04
![]() Alert Antivirus Attack Computer Virus Business Flow Chart
Alert Antivirus Attack Computer Virus Business Flow Chart
 The Logic Structure Of Virus Download Scientific Diagram
The Logic Structure Of Virus Download Scientific Diagram
 Could We Contain Hate Speech Like A Computer Virus Technology
Could We Contain Hate Speech Like A Computer Virus Technology
 Computer Threats Business Venn Diagram Management Strategy
Computer Threats Business Venn Diagram Management Strategy
Types Of Computer Virus With Examples
 Online Hate Speech Could Be Contained Like A Computer Virus Say
Online Hate Speech Could Be Contained Like A Computer Virus Say
 Virus Computer Code Program Diagram Flat Technology Objects
Virus Computer Code Program Diagram Flat Technology Objects
What Are The Similarities Between Computer Viruses And Biological
 The Evolution Of Computer Viruses Cheeky Munkey
The Evolution Of Computer Viruses Cheeky Munkey
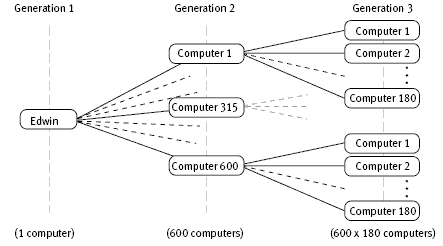
 Why Japan S Search And Destroy Cyber Weapon Could Be A Very Bad
Why Japan S Search And Destroy Cyber Weapon Could Be A Very Bad
![]() Alert Antivirus Attack Computer Virus Business Flow Chart
Alert Antivirus Attack Computer Virus Business Flow Chart
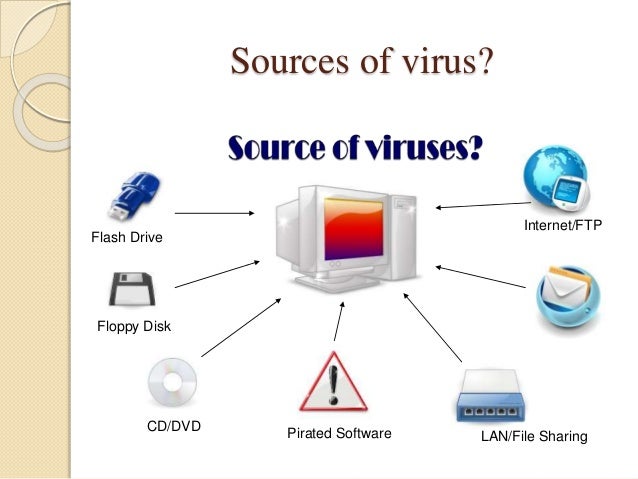 Antivirus Virus Detection And Removal Methods
Antivirus Virus Detection And Removal Methods
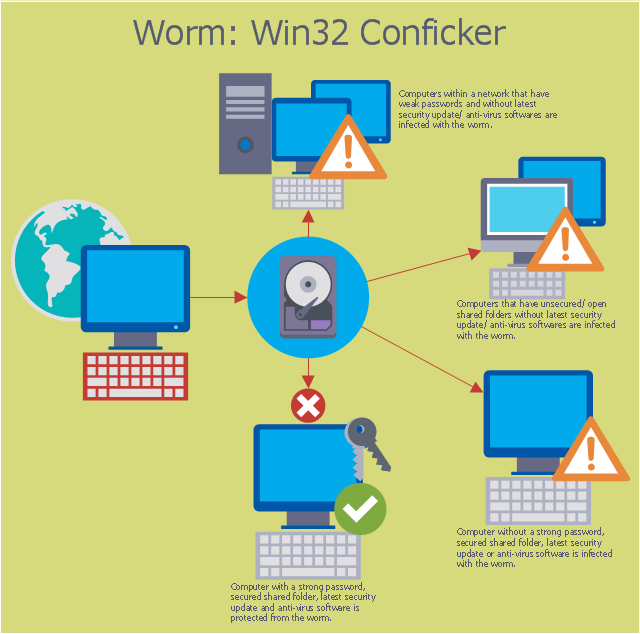
It S Conficker Worm Virus Day Borderstan
![]() Alert Antivirus Attack Computer Virus Business Flow Chart
Alert Antivirus Attack Computer Virus Business Flow Chart
Computer System And Virus Scan Method Diagram Schematic And
 Figure 1 Fractional Dynamics Of Computer Virus Propagation
Figure 1 Fractional Dynamics Of Computer Virus Propagation
 Ipa Information Technology Promotion Agency Japan Ipa Isec In
Ipa Information Technology Promotion Agency Japan Ipa Isec In
 Diagram Of Computer Security Stock Photograph K17526256 Fotosearch
Diagram Of Computer Security Stock Photograph K17526256 Fotosearch
 Antivirus Software Computer Virus Computer Software Esquema
Antivirus Software Computer Virus Computer Software Esquema
 Diagram Showing Different Kinds Of Viruses Ipad Case Skin By
Diagram Showing Different Kinds Of Viruses Ipad Case Skin By
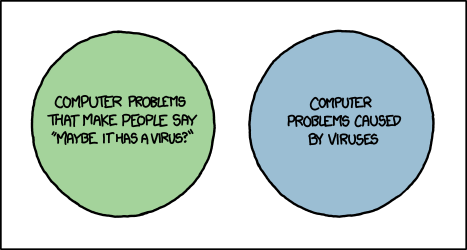
 Cliff Pickover On Twitter Computer Virus Venn Diagram Xkcd
Cliff Pickover On Twitter Computer Virus Venn Diagram Xkcd
 Rombertik Virus Horrifying Suicidal Malware Which Demolishes Pc
Rombertik Virus Horrifying Suicidal Malware Which Demolishes Pc
 Ipa Information Technology Promotion Agency Japan Ipa Isec In
Ipa Information Technology Promotion Agency Japan Ipa Isec In
 Basic Computer Skills What To Do If Your Computer Gets A Virus
Basic Computer Skills What To Do If Your Computer Gets A Virus
 How To Get Virus Off The Computer Comodo Virus Removal Software
How To Get Virus Off The Computer Comodo Virus Removal Software
Our Rundown Of The Top Five Worst Computer Viruses Certus

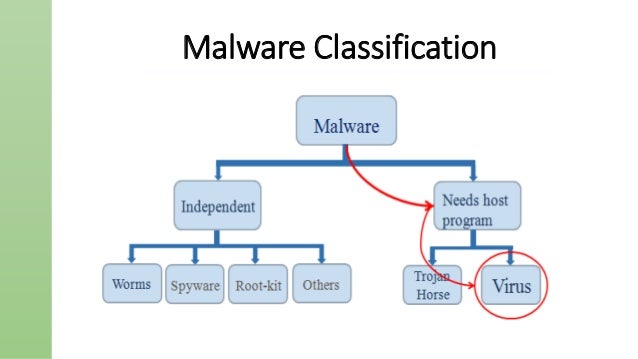 Computer Viruses And Protections
Computer Viruses And Protections
 Virus A Retrospective Social Impact
Virus A Retrospective Social Impact
 Pseudo Code Of A Computer Virus 1 Download Scientific Diagram
Pseudo Code Of A Computer Virus 1 Download Scientific Diagram
Performance Investigation Of Antivirus A Comparative Analysis
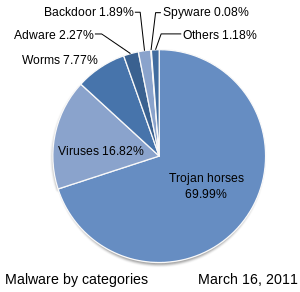
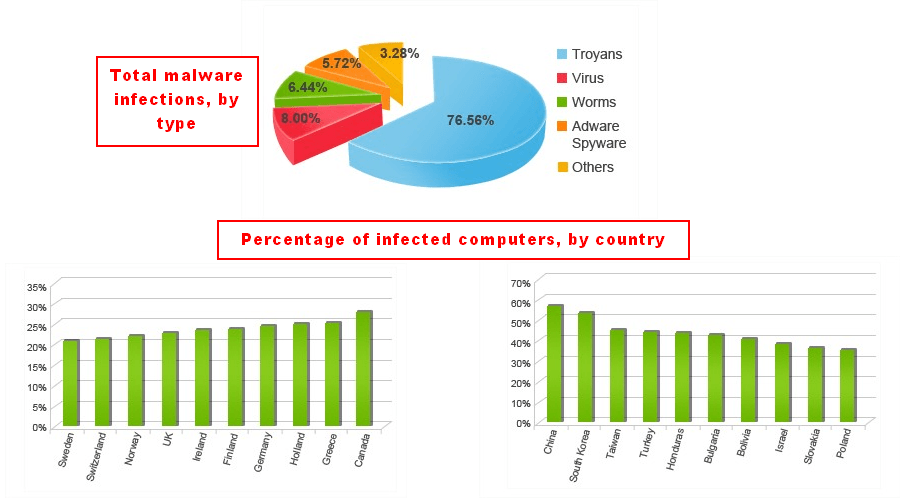 32 Of Computers Around The World Are Infected With Viruses And
32 Of Computers Around The World Are Infected With Viruses And
 Are Computer Viruses Alive Quora
Are Computer Viruses Alive Quora
So I Have This Virus Graphjam Funny Graphs
 Patent Report Us9906550 Computer Virus Protection
Patent Report Us9906550 Computer Virus Protection
Important Steve The Computer Guy
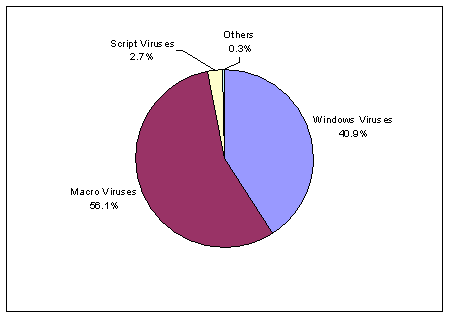
 Computer Viruses Infographics Visual Ly
Computer Viruses Infographics Visual Ly
 Pdf Computer Virus And Protection Methods Using Lab Analysis
Pdf Computer Virus And Protection Methods Using Lab Analysis
 Computer Virus Supinfo Ecole Superieure D Informatique
Computer Virus Supinfo Ecole Superieure D Informatique
 Ipa Information Technology Promotion Agency Japan Ipa Isec In
Ipa Information Technology Promotion Agency Japan Ipa Isec In
Anti Virus Method Computer And Recording Medium Diagram
 Remove Malware Spyware And Viruses From Your Pc Guide To
Remove Malware Spyware And Viruses From Your Pc Guide To
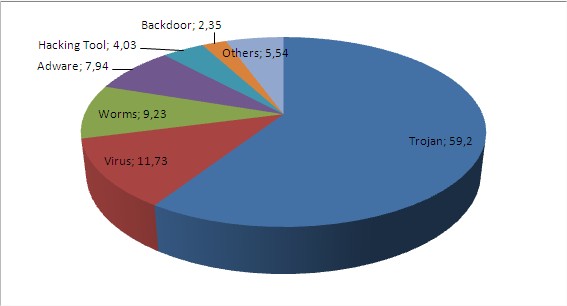 In January 50 Percent Of Computers Scanned By Panda Activescan
In January 50 Percent Of Computers Scanned By Panda Activescan
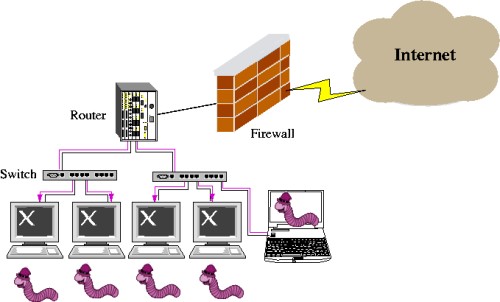 Ccna Security Worm Virus And Trojan Horse Attacks
Ccna Security Worm Virus And Trojan Horse Attacks
 Virus A Retrospective Social Impact
Virus A Retrospective Social Impact
/cdn.vox-cdn.com/assets/758332/duqu-trojan-design.jpg) Duqu Computer Trojan Spy May Be Based On Stuxnet The Verge
Duqu Computer Trojan Spy May Be Based On Stuxnet The Verge
 Uml Diagram Of Embedded Target Profile And Annaakournikova
Uml Diagram Of Embedded Target Profile And Annaakournikova
 Ipa Information Technology Promotion Agency Japan Ipa Virus
Ipa Information Technology Promotion Agency Japan Ipa Virus
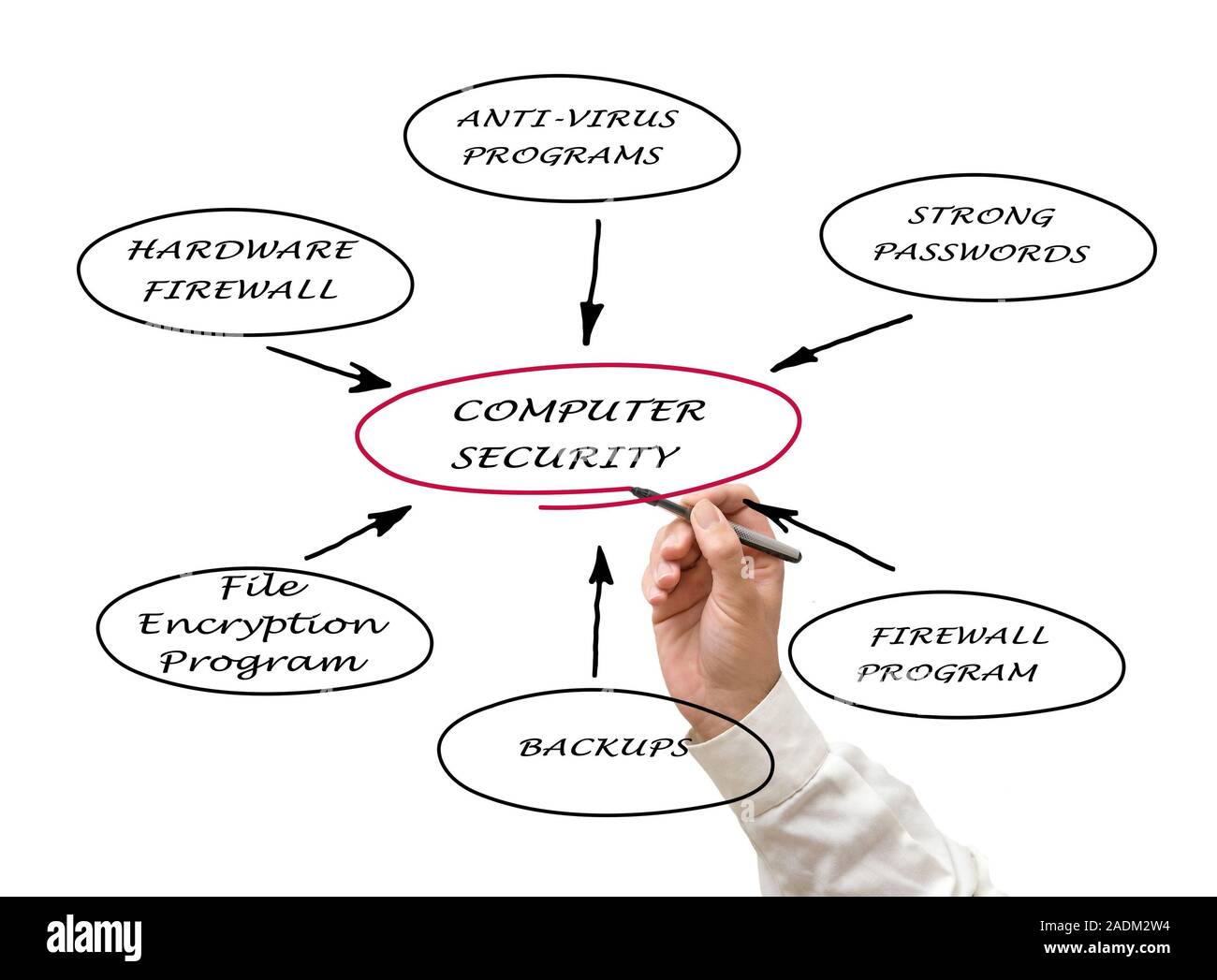 Diagram Of Computer Security Stock Photo 335428832 Alamy
Diagram Of Computer Security Stock Photo 335428832 Alamy
 Figure 3 From Node Centrality Analysis Of Multiplex Networks Under
Figure 3 From Node Centrality Analysis Of Multiplex Networks Under







Komentar
Posting Komentar